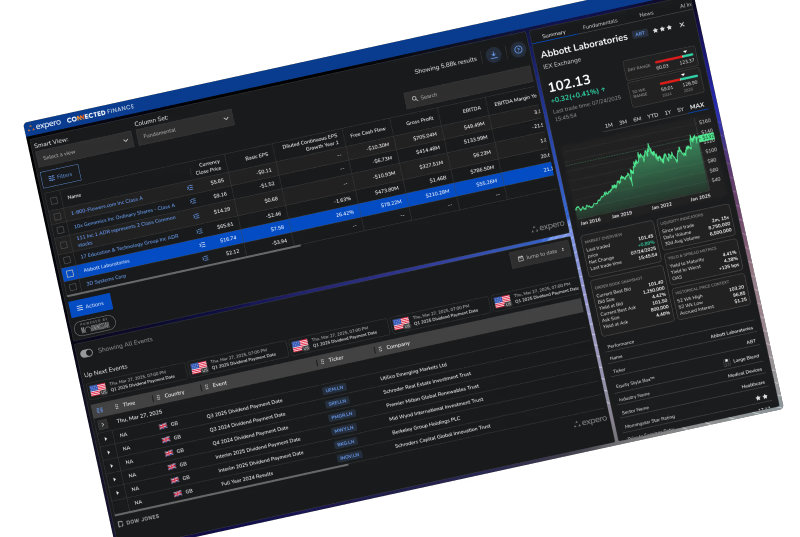
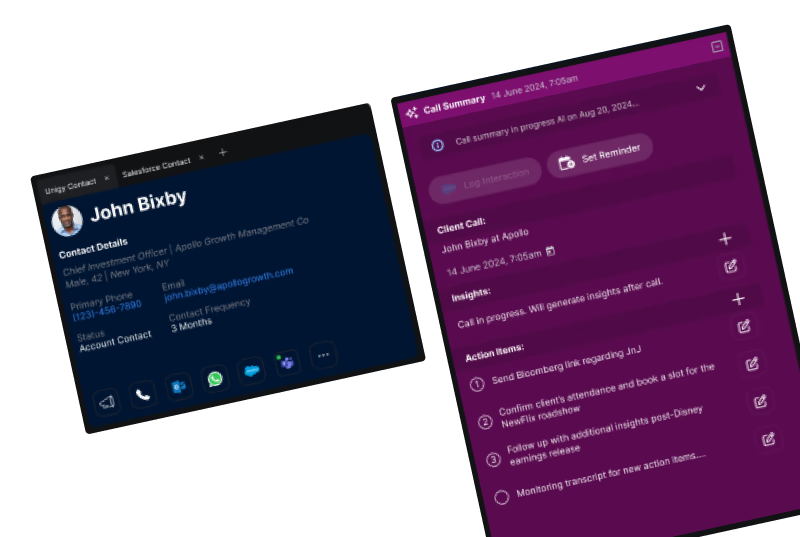
The Front Ends That Power Finance
Building high-performance user experiences for wealth management, asset management, brokerage, and beyond.
Expero helps you drive smarter decisions and better outcomes
Unforgettable User Experiences
We transform your existing data into immersive interfaces that captivate, resonate, and scale.
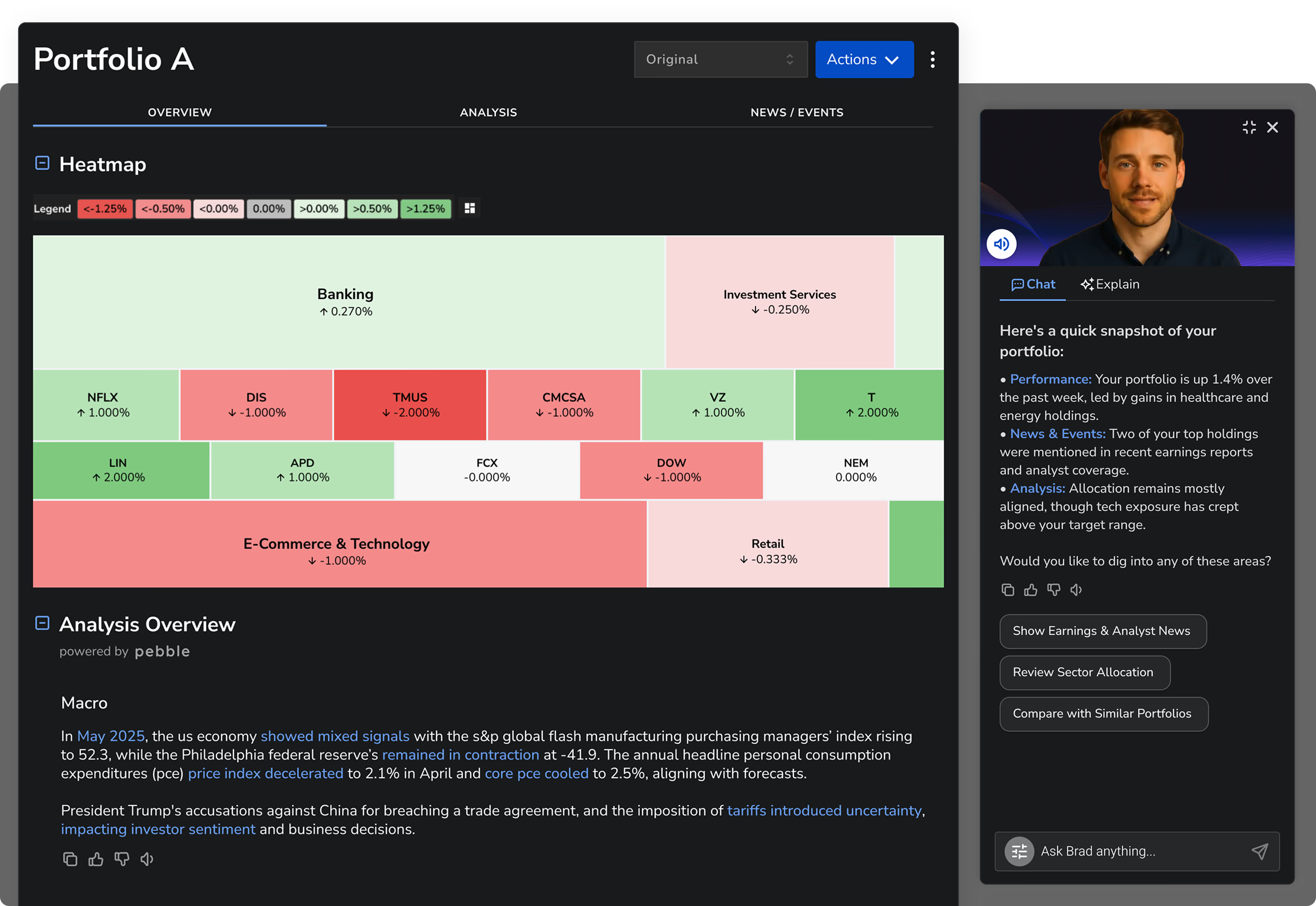

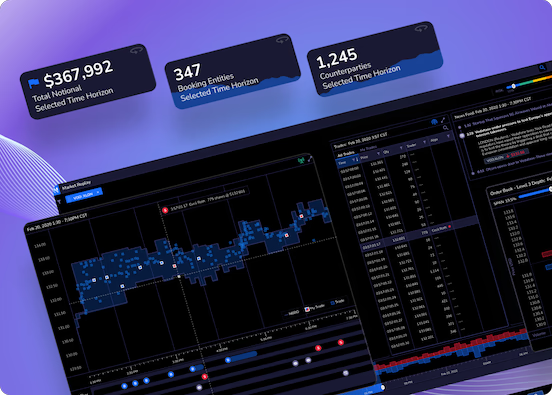
Rapid Time to Market
Our plug-and-play software components, proven development frameworks, and experienced team enable faster, more efficient platform and app launches.
Collaboration to the Core
Breakthrough outcomes demand team effort. We work closely with your product and development teams, as well as a range of leading industry partners, driving innovation and alignment at every step.




Delivering everything you need from targeted enhancements to full-scale, innovation-driven transformations that drive lasting impact

Our Work
We’ve delivered unforgettable user experiences for a host of leading financial firms. Discover what you can build with Expero.

Designing the Future of Finance
Decision Support Comes of Age: From Guidance to Design
CIRO’s updated OEO guidance marks a shift toward compliant decision support in self-directed platforms. Learn how contextual guidance, design-led tools, and always-on support can improve investor confidence without crossing into advice.
From Static to Dynamic: How AI Is Transforming Financial User Experiences
Generative AI is transforming financial UX from static dashboards into dynamic, decision-making partners. Instead of relying on users to interpret data, AI-driven interfaces proactively surface insights, adapt to context, and learn from behavior. This shift redefines the front end as a collaborator that serves experts who need transparency, everyday users who need clarity, and machines that will consume data directly. The firms that succeed will balance automation with human judgment while applying intelligence with purpose, rigor, and imagination.
At the Forefront: Fintech Conversations, Episode 87: The Front Ends That Power Finance
The conversation covers Expero’s recent pivot to focus exclusively on finance, its collaborative, multidisciplinary approach to product design and the growing role of predictive UX and generative AI in shaping the next generation of financial interfaces.
Accelerate Your Business. Get in Touch.
Have a vision? Tell us what you’d like to build and one of our experts will get back to you.